MeshBeacon: Because Your Mesh Network Should Actually DO Something

Take It. Make It Yours.
MeshBeacon is open source. Every line of it.
I didn’t build this so it could run on one node in San Jose. I built it so it could run everywhere. Fork the repository. Change the coordinates to your city. Add your local weather stations. Point the earthquake monitor at your fault lines. Write a new broadcast module for something I haven’t thought of yet.
DataSage: The Proof-of-Concept That Took on a Life of it's Own
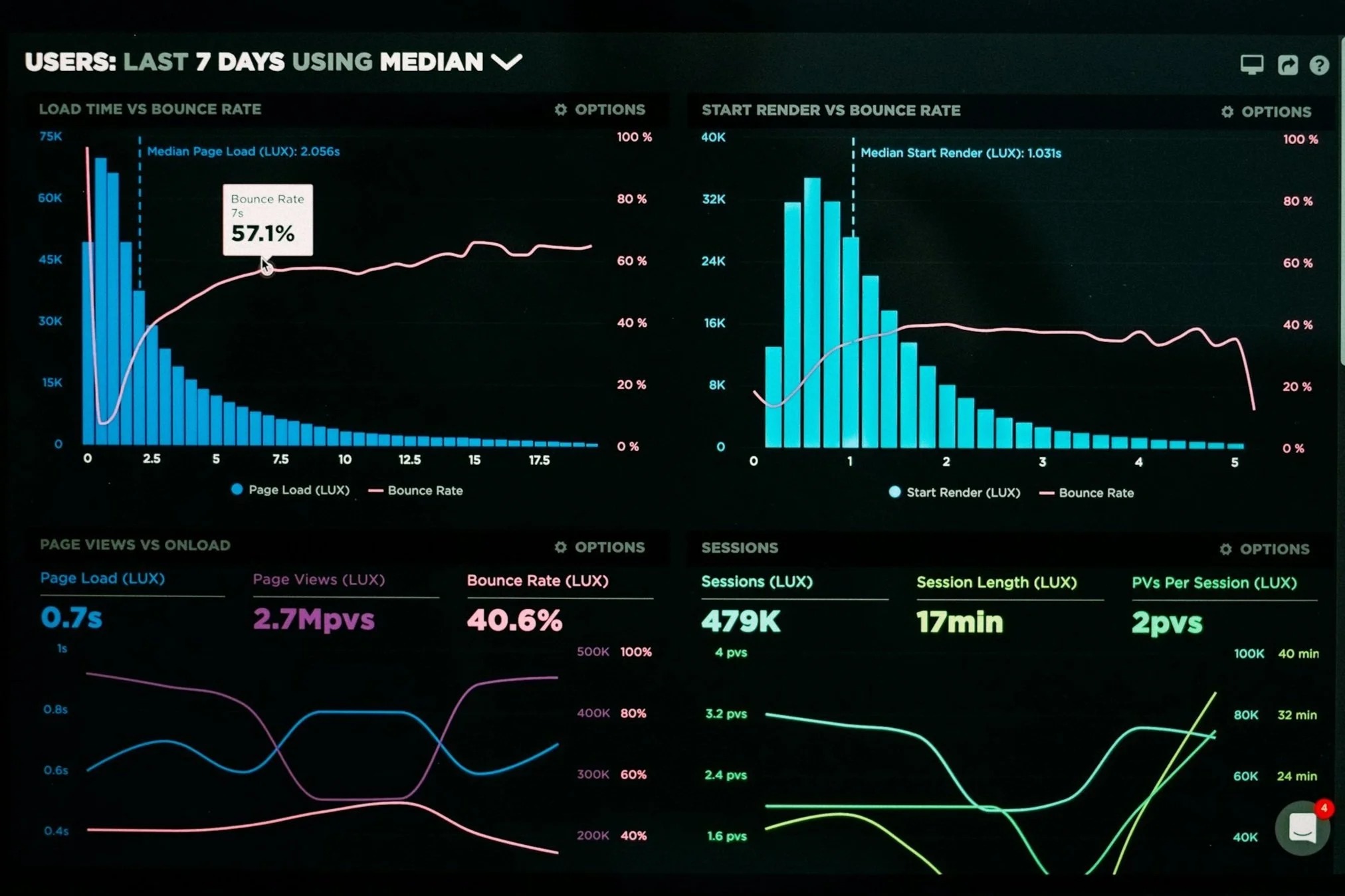
The “Aha!” Moment That Started This Journey
You know, I’ve spent my career believing that technology should empower everyone, not just the experts. That’s why, when I started working with data analytics at Stanford, I kept thinking about my days at Apple Computer, trying to understand a bill of materials in an Excel spreadsheet. Margins up, expenses down—but what did it all mean? What was the story those numbers were trying to tell?
MeshCore vs Meshtastic: Why One Actually Works When You NEED It To Work
 You know what REALLY grinds my gears? And I mean REALLY makes me want to throw a radio into the ocean? It’s when people ask me, “Hey, what’s the difference between MeshCore and Meshtastic?”
You know what REALLY grinds my gears? And I mean REALLY makes me want to throw a radio into the ocean? It’s when people ask me, “Hey, what’s the difference between MeshCore and Meshtastic?”
OH, WHERE DO I BEGIN?!
It’s like asking what’s the difference between a surgeon and a guy with a chainsaw! Sure, they BOTH make cuts, but ONE of them knows when to STOP CUTTING!
Unleashing the Potential of Decentralized Communication: A Deep Dive into LoRa Meshtastic Networks
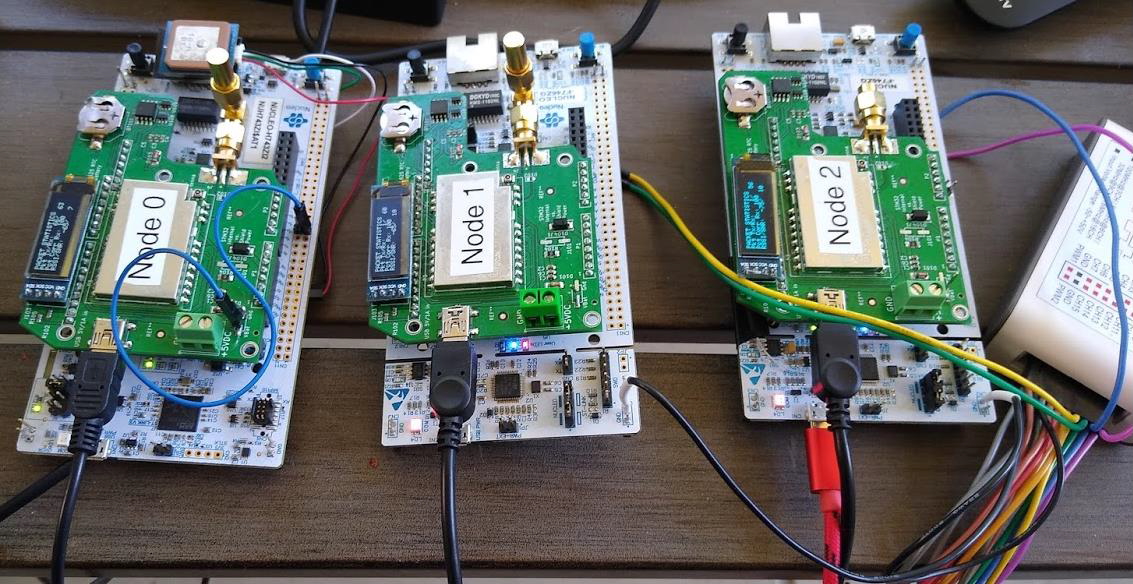 In our increasingly interconnected digital world, networking has progressed far beyond conventional wired and centralized configurations. Leading this transformation are LoRa Meshtastic networks—a flexible, robust, and sustainable solution for long-distance communication. Let’s explore the intricacies of this network, its advantages, and the essential equipment needed to utilize its full potential.
In our increasingly interconnected digital world, networking has progressed far beyond conventional wired and centralized configurations. Leading this transformation are LoRa Meshtastic networks—a flexible, robust, and sustainable solution for long-distance communication. Let’s explore the intricacies of this network, its advantages, and the essential equipment needed to utilize its full potential.
What is a LoRa Meshtastic Network?
LoRa (Long Range) is a spread-spectrum modulation technique derived from chirp spread spectrum (CSS) technology. It is known for its capability to deliver exceptionally long-range data transmission with low power consumption. Meshtastic, an open-source project, leverages LoRa technology to create a decentralized mesh network. This empowers users to exchange messages and relay data over extensive distances without relying on conventional telecommunication infrastructures.
Charting a Path to Success: Guide for Aspiring Business Intelligence Analysts and Data Engineers
As the digital economy continues to expand, driven by vast amounts of data, the roles of Business Intelligence (BI) Analysts and Data Engineers have become increasingly pivotal. For those looking to thrust themselves into these dynamic and rewarding careers, it requires a multidimensional approach encompassing skill acquisition, portfolio development, networking, and continuous learning.
This comprehensive guide delves into the quintessential elements that will aid aspiring BI Analysts and Data Engineers in effectively navigating their career journey. Whether you’re a college graduate, a mid-career professional seeking to pivot, or a data enthusiast passionate about making impactful, data-driven decisions, these insights will be indispensable to your professional ascent.
The Cult of Politics: Why Blind Allegiance is Dangerous

In recent years, my political observations have led me to a rather disheartening conclusion: the leaders we elect, regardless of their political affiliation, often appear to crave power above all else. This desire for dominance manifests in a refusal to collaborate across party lines, breeding a culture of division and distrust. This blog post aims to explore the striking resemblance between blind political allegiance and cult-like behavior, as well as how this polarization has eroded our national discourse. Reflecting on historical periods of political division, we can also glean valuable lessons for healing and unity.
The Impact of Artificial Intelligence on Business Intelligence
 In the rapidly evolving landscape of digital transformation, a phenomenon of profound significance has taken center stage: the integration of Artificial Intelligence (AI) into the realm of Business Intelligence (BI). This integration has emerged as a formidable force that not only propels strategic innovation but also fundamentally reshapes the very fabric of how organizations operate, particularly in the face of mounting complexities stemming from data proliferation. As companies grapple with the challenges of extracting meaningful insights from vast, diverse, and often disorganized datasets, AI stands out as a transformative agent. It enhances BI’s capabilities, fundamentally altering the ways in which organizations glean insights, make informed decisions, and strategically maintain competitive advantages in their respective markets. This document aims to provide an in-depth exploration of the profound impact that AI has on BI, drawing insights from a seasoned Silicon Valley perspective and highlighting noteworthy examples that underscore pivotal advancements along with their practical implications.
In the rapidly evolving landscape of digital transformation, a phenomenon of profound significance has taken center stage: the integration of Artificial Intelligence (AI) into the realm of Business Intelligence (BI). This integration has emerged as a formidable force that not only propels strategic innovation but also fundamentally reshapes the very fabric of how organizations operate, particularly in the face of mounting complexities stemming from data proliferation. As companies grapple with the challenges of extracting meaningful insights from vast, diverse, and often disorganized datasets, AI stands out as a transformative agent. It enhances BI’s capabilities, fundamentally altering the ways in which organizations glean insights, make informed decisions, and strategically maintain competitive advantages in their respective markets. This document aims to provide an in-depth exploration of the profound impact that AI has on BI, drawing insights from a seasoned Silicon Valley perspective and highlighting noteworthy examples that underscore pivotal advancements along with their practical implications.
Automating Data Workflows with Apache Airflow

In the realm of data engineering, the ability to automate workflows is a game changer. Imagine waking up every morning with the assurance that your data pipelines have been seamlessly executed, data has flowed flawlessly from one system to another, and your business insights are ready for you to act on. No more late-night database updates or cross-eyed mornings debugging cron jobs. Enter Apache Airflow, the Swiss Army knife for automating and orchestrating complex workflows.
Repositories, what are they good for?

In recent years, the importance of repositories like GitHub has become increasingly apparent in the tech industry. Platforms such as GitHub, GitLab, and BitBucket are web-based hosting services that provide version control and collaboration features for software development projects. These platforms allow developers to store and manage their code, track changes, collaborate with others, and contribute to open-source projects. In this expanded article, we’ll deeply discuss the significance of repositories like GitHub and provide comprehensive instructions on how to use a repository effectively.
Data Engineering: Big Data Transfer
Are you aspiring to be a Data Engineer or Data Scientist? Welcome to an exclusive club where the real journey begins with acquiring deep domain knowledge, particularly about one of the most critical facets of data management: the transfer of substantial datasets. This guide aims to introduce you to advanced data transfer techniques, integral tools, and best practices that make up a data engineer’s arsenal.
We have all heard the tales of engineers manipulating massive datasets in today’s rapidly evolving technological landscape. Data Engineers (DEs), the unsung heroes in the data science ecosystem, form the backbone of robust research, analytics, and data science operations. Without the diligence and expertise of DEs, the field of data science would be virtually nonexistent. Analogically, data engineers can be thought of as the bass guitarists in a rock band, providing the foundational rhythm and melodic complexity that propels the band forward. Alternatively, they are akin to Dwight Schrute supporting Michael Scott in “The Office”. While many may aspire to be the lead singer (data scientist), they often overlook the crucial support roles like that of a data engineer. People frequently ask, “What is the first step in becoming a data engineer?” My answer invariably focuses on mastering data transfer techniques. With an array of options available, I will expound upon the methodologies I utilize in my professional practice.